GPS Spoofing: is your high-end receiver safe from an attack?

Threats from jammers have long worried GNSS users. And, now, a new GNSS bogeyman is here…spoofers. Unlike jamming, which attempts to block GNSS signals, spoofers are altogether far more sinister.
By replicating GNSS signals, a spoofer can fool a receiver into thinking that it’s elsewhere in either time or location.
And, given a growing reliance on GNSS technology for positioning and timing, it’s not hard to imagine the potential havoc a spoofing attack might cause.
$150 SDRs bring spoofing to the masses
Traditionally, spoofing is an expensive pursuit. A GPS simulator, with a price tag in the tens of thousands of dollars, is usually enough to put off most would-be spoofers.
But the now affordable price of this technology is changing the landscape.
In 2013, a team of researchers from the University of Texas commandeered a 213‑foot yacht using $3,000 worth of equipment.
The arrival of cheap Software Defined Radios (SDR) and open-source code availability is making spoofing more accessible.
Signs of spoofing
If a smartphone provides positioning, the first inkling of a spoofing attack is the phone reporting an obviously wrong location.
Figure 1 shows an example of an attacker spoofing an iPhone6 into reporting its position at the top of Mount Everest.
It was harder to spoof an Acer Android phone. The Acer uses additional positioning information from WiFi and the cellular network.
During this test, the phone owner’s wife was alerted via Facebook that he had left the country.But, spoofing a trip to North Korea might have a slightly less amusing outcome.

In the case of high-end receivers that use multiple frequencies from several satellite constellations, spoofing is more challenging. Below are signs to look for if there is suspicion of spoofing.
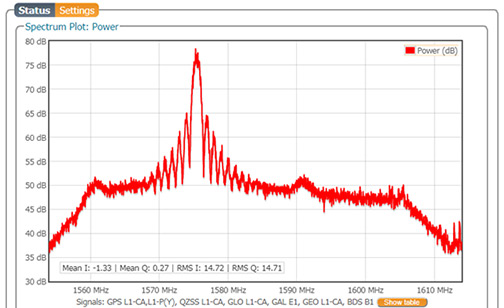
1) The spoofed signal is visible in the RF spectrum
The low power of GPS signals means that they are barely discernible from the thermal noise background.
In order to spoof a receiver, the SDR signals are transmitted with a much higher power making them clearly visible above the background as Figure 2 shows.
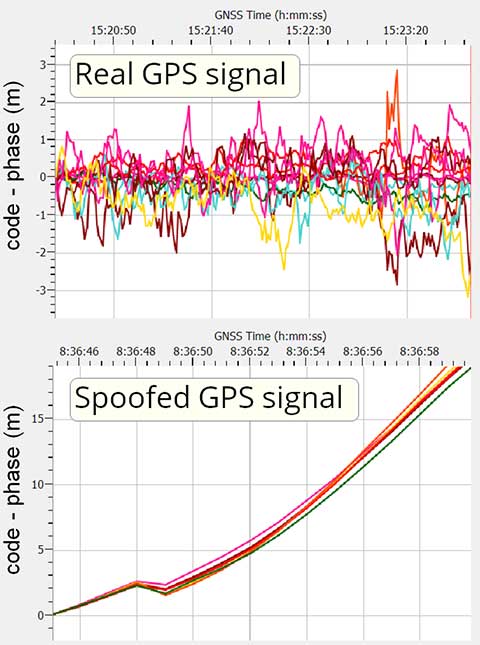
2) Divergent code minus carrier behavior
Over short time frames, satellite distances measured using the code and carrier phase of the satellite signals should show very little difference – Figure 3 (upper panel).
This behavior is difficult to replicate. So, spoofed signals exhibit a difference that can increases rapidly over a short period of time – Figure 3 (lower panel).
3) Incomplete and inaccurate nav data
Spoofed satellite navigation data is often missing the GPS constellation almanac and is still only a vague match for the real navigation data.
4) Jamming of Glonass and/or L2
Spoofing techniques are advancing but at the moment, only the GPS L1 signal is spoofed so a common tactic is to additionally jam the L1 Glonass frequencies and the L2 band. This will manifest as a sudden fallback to a GPS only standalone mode.
What can receivers do about spoofing?
As shown, single-frequency, low-end devices and smartphones are relatively easy to spoof. High-end multi-frequency receivers aren’t so easy. These high-end receivers offer a number of tricks to detect spoofing.
However, in the event such a receiver detects spoofing, what exactly can it do?
1) Signal integrity alerting
High-end receivers have the option of employing spoofing flags. As such, the receiver can alert the user if it detects a spoofing attack directly in the RF spectrum or in the GPS measurements.
2) Frequency diversity
If the receiver detects spoofing on one frequency, it can switch to using measurements from other frequencies. Thereby, effectively ignoring the spoofed frequency.
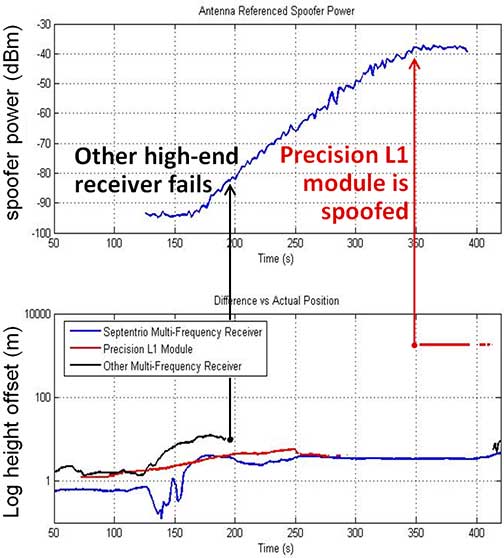
Figure 4 shows this technique in action.
Three receivers are subject to GPS L1 spoofing. As the spoofer power increases, the Septentrio AsteRx4 receiver detects the spoof on L1. At this point, it switches from an L1/L2 to an L2/L5 PVT and successfully maintains an accurate position.
The other multi-frequency receiver also detects a problem. However, it has no alternative dual-frequency solution so simply stops outputting a PVT.
The L1-only module, with no detection mechanisms, switches to tracking the spoofed signal and its position gets spoofed.
3) Inertial sensor integration
An IMU device, either coupled to the receiver or mounted on the board itself, provides a unambiguous check for spoofing. In the presence of spoofing, IMUs can also provide input for an integrated PVT solution to mitigate the effects of spoofing.
Staying one step ahead
High-end GNSS receivers, particularly those employing spoofing detection and mitigation methods are still relatively safe from spoofers.
However, the increasing sophistication of both hardware — in the form of SDRs and open-source software — means there’s no room for complacency.

